Hash functions are cornerstone elements in the field of cryptography and data integrity, playing pivotal roles in various applications, including blockchain technology, digital signatures, and data provenance. Among the multitude of hash functions, SHA-256 and SHA-3 stand out as two of the most widely used algorithms today. This article aims to compare SHA-256 and SHA-3 by examining their structures, performance, security features, and applications in data provenance, highlighting the pros and cons of each.
Overview of SHA-256
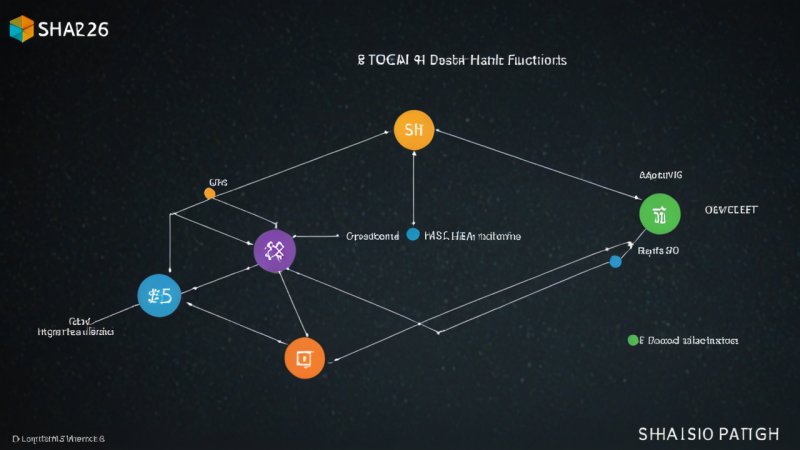
SHA-256, part of the SHA-2 family, was developed by the National Security Agency (NSA) and published by the National Institute of Standards and Technology (NIST) in 2001. It produces a 256-bit hash value and is widely used in various security applications and protocols, including SSL/TLS, PGP, and blockchain technology such as Bitcoin. The algorithm operates through a series of logical functions and bitwise operations, ensuring that even a small change in input produces a significantly different hash output.
Pros of SHA-256
- Security: SHA-256 has proven to be secure against collision attacks, making it reliable for data integrity verification.
- Performance: While it is slower than some alternatives, its performance is reasonable for many applications, particularly in the blockchain space.
- Established Trust: Being a long-standing standard, SHA-256 is well-understood and widely accepted, especially in the cryptocurrency realm.
Cons of SHA-256
- Speed: In comparison to newer algorithms, SHA-256 can be slower, particularly in environments requiring high throughput.
- Bit-length Limitation: The fixed 256-bit output may not meet the needs of applications requiring larger hash sizes for enhanced security.
Overview of SHA-3
SHA-3, standardized in 2015, represents a significant evolution in hash function design. Developed by Guido Bertoni, Joan Daemen, Michaël Peeters, and Gilles Van Assche, SHA-3 is based on a different underlying structure known as the Keccak sponge construction. It offers flexibility in output length, allowing for hash values of varying sizes, including 224, 256, 384, and 512 bits.
Pros of SHA-3
- Security: SHA-3 is designed to be resistant to various cryptographic attacks, including collision, pre-image, and second pre-image attacks.
- Flexibility: With varying output lengths, SHA-3 can be tailored to meet specific application requirements.
- Performance in Hardware: SHA-3 is optimized for efficient implementation in hardware environments, often outperforming SHA-256 in such contexts.
Cons of SHA-3
- Adoption: As a newer standard, SHA-3 has not yet achieved the same level of acceptance as SHA-256, particularly in legacy systems.
- Implementation Complexity: The sponge construction can be more complex to implement than the Merkle-Damgård structure used by SHA-256.
Comparison of Security Features
Both SHA-256 and SHA-3 provide strong security guarantees, but they approach these guarantees differently. SHA-256's security comes from its resistance to collision and pre-image attacks, bolstered by its long-standing use and analysis in the cryptographic community. In contrast, SHA-3's innovative design aims to address potential vulnerabilities associated with the Merkle-Damgård construction, providing a robust alternative.
Performance Comparison
In terms of performance, SHA-256 tends to be slower than SHA-3, especially in software implementations. However, SHA-3 can excel in hardware implementations due to its sponge construction, which allows for efficient processing. The choice between the two can depend on the specific use case; for large-scale applications needing high speed, SHA-3 may be preferred, while SHA-256 remains a solid choice for environments where security and trust are paramount.
Applications in Data Provenance
Data provenance refers to the documentation of the origins and history of data, crucial for maintaining data integrity and trustworthiness. SHA-256 is widely used in blockchain systems, ensuring the integrity of transactions and data blocks. On the other hand, SHA-3 is emerging in various applications, particularly those requiring flexible hash sizes or that leverage its efficient hardware performance.
Conclusion
In summary, both SHA-256 and SHA-3 have their unique strengths and weaknesses that make them suitable for different applications in the realm of data provenance and cryptography. SHA-256 remains a reliable and well-understood choice for many existing systems, particularly in blockchain technology. However, SHA-3 offers innovative features and performance advantages that make it an appealing option for future applications. Ultimately, the choice between SHA-256 and SHA-3 will depend on the specific needs of the application, considering factors such as security requirements, performance constraints, and the maturity of the environment in which the hash function will be implemented.