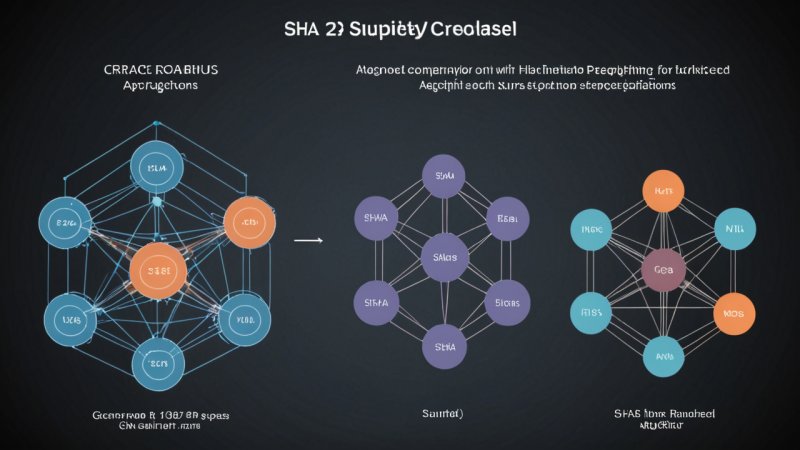
In the realm of data security, cryptographic hashing algorithms play a pivotal role in ensuring data integrity and security. Among the myriad of hashing algorithms available, SHA-256 and SHA-3 are two of the most prominent and widely used. This article aims to provide a comparative analysis of these two hashing algorithms, exploring their characteristics, strengths, weaknesses, and applications in various domains such as blockchain technology, data integrity, and password storage.
Overview of SHA-256
SHA-256 (Secure Hash Algorithm 256-bit) is part of the SHA-2 family, developed by the National Security Agency (NSA) and published in 2001. It produces a fixed-size 256-bit hash value and is widely used in various security applications and protocols, including SSL/TLS and cryptocurrency.
Characteristics of SHA-256
- Bit Length: 256 bits
- Output Size: 64 hexadecimal characters
- Speed: Relatively fast on modern hardware
- Collision Resistance: Extremely high; finding two different inputs that produce the same hash is computationally infeasible
Applications of SHA-256
SHA-256 is extensively used in blockchain technology, particularly in Bitcoin, where it ensures the integrity and security of transactions. It is also employed in digital signatures, certificates, and various security protocols.
Overview of SHA-3
SHA-3 (Secure Hash Algorithm 3) was released in 2015 and is the latest member of the Secure Hash Algorithm family. Unlike SHA-2, which is based on the Merkle-Damgård structure, SHA-3 uses a different approach called the sponge construction, which offers new functionalities and security advantages.
Characteristics of SHA-3
- Bit Length: Supports variable output lengths (224, 256, 384, and 512 bits)
- Output Size: Varies based on the specified bit length
- Speed: Generally slower than SHA-256, but offers greater flexibility
- Collision Resistance: High; designed to withstand various attack vectors
Applications of SHA-3
SHA-3 is recommended for new applications due to its innovative design and strong security properties. It is used in blockchain, digital signatures, and data integrity checks, among other areas.
Comparative Analysis
Security
Both SHA-256 and SHA-3 provide robust security features, but their underlying structures differ significantly. SHA-256 has been extensively analyzed and is currently considered secure; however, its design is susceptible to certain attack strategies. In contrast, SHA-3's sponge construction offers a more flexible and potentially more secure alternative, especially against future quantum attacks.
Performance
In terms of performance, SHA-256 generally outperforms SHA-3 in speed, making it more suitable for applications where quick hashing is essential, such as in high-frequency trading platforms or real-time data processing. However, SHA-3’s versatility allows for adjustable output sizes, which can be an advantage in specific use cases.
Flexibility
SHA-3’s ability to support multiple output sizes makes it a more versatile choice for developers looking to tailor their hashing needs. For instance, applications requiring smaller hash outputs can utilize SHA-3-224 or SHA-3-256, while those needing longer hashes can opt for SHA-3-384 or SHA-3-512. In contrast, SHA-256 is limited to a fixed output size.
Implementation
SHA-256 is widely implemented across various platforms and programming languages, which makes it easier for developers to integrate into their systems. SHA-3, being newer, may have less widespread support, although its adoption is growing. Both algorithms are implemented in libraries such as OpenSSL and are supported by many programming environments.
Case Studies
Use of SHA-256 in Bitcoin
Bitcoin, the pioneering cryptocurrency, utilizes SHA-256 for securing transactions and mining. Each block in the blockchain contains the SHA-256 hash of the previous block, linking them together and ensuring data integrity. The algorithm's speed and security features have made it a cornerstone of Bitcoin's decentralized network.
Adoption of SHA-3 in Modern Applications
SHA-3 has been gaining traction in modern applications, particularly in scenarios requiring high security and flexibility. For example, blockchain projects that prioritize advanced security features are increasingly adopting SHA-3 to protect against future vulnerabilities.
Conclusion
In summary, both SHA-256 and SHA-3 are powerful cryptographic hashing algorithms with distinct advantages and use cases. SHA-256 is well-established, fast, and widely adopted, making it ideal for applications where speed is crucial. On the other hand, SHA-3 offers innovative features and enhanced flexibility, positioning it as a strong candidate for future applications requiring high security and adaptability. Ultimately, the choice between SHA-256 and SHA-3 should be guided by specific project requirements, including security needs, performance expectations, and the desired output characteristics.