MD5
MD5 (Message-Digest Algorithm 5) is a widely used cryptographic hash function that produces a 128-bit hash value. Despite its historical significance, it is now considered weak due to vulnerabilities found over time, leading to a decline in its use in security applications.
Artificial Intelligence Ethics
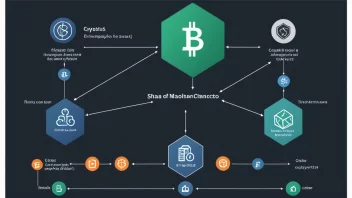
Understanding Cryptographic Hashing Algorithms: Their Role in Blockchain, Data Integrity, and Password Security

Artificial Intelligence Ethics
Understanding Cryptographic Hashing Algorithms: Key Concepts and Applications